Advertisements
Security attacks
Taxonomy of attacks with relation to security goals
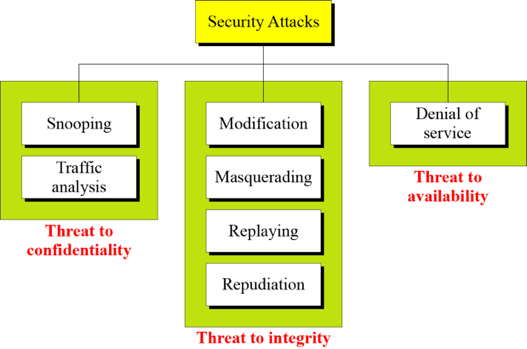
Attacks Threatening Confidentiality
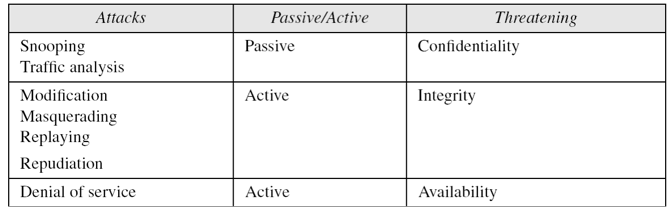
- Snooping refers to unauthorized access to or interception of data.
- Traffic analysis refers to obtaining some other type of information by monitoring online traffic.
Attacks Threatening Integrity
- Modification means that the attacker intercepts the message and changes it.
- Masquerading or spoofing happens when the attacker impersonates somebody else.
- Replaying means the attacker obtains a copy
- of a message sent by a user and later tries to replay it.
- Repudiation means that sender of the message might later deny that she has sent the message; the receiver of the message might later deny that he has received the message.
Attacks Threatening Availability
- Denial of service (DoS) is a very common attack. It may slow down or totally interrupt the service of a system.
Active & Passive Attack:
- A passive attack is one in which the intruder eavesdrops but does not modify the message stream in any way.
- An active attack is one in which the intruder may transmit messages, replay old messages, modify messages in transit, or delete selected messages from the wire.
Categorization of passive and active attacks
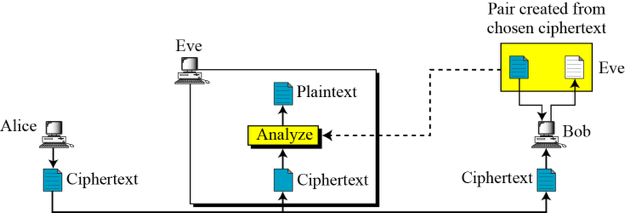
Brute Force & Cryptanalysis attacks
Brute- Force Attack:
- The attacker tries every possible key on a piece of cipher text until an intelligible translation into plain text is obtained.
- Trial and error method is followed.
|
Cryptanalysis Attacks |
Known to crypt analyst |
|
Ciphertext only attack |
Encryption algorithm & cipher text |
|
Known plain text attack |
Encryption algorithm & cipher text & (C,P) Pair |
|
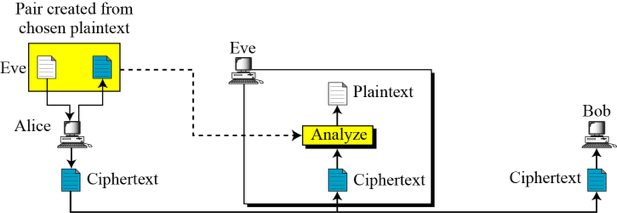
Chosen Plain text attack |
Encryption algorithm & cipher text & (Plain text chosen by cryptanalyst with its ciphertext and key) |
|
Chosen Cipher text attack |
Encryption algorithm & cipher text & (Cipher text chosen by cryptanalyst with its plain text and key) |
|
Chosen text attack (Chosen Plain text attack + Chosen Cipher text attack) |
Encryption algorithm & cipher text & (Cipher text chosen by cryptanalyst with its plain text and key) & (Plain text chosen by cryptanalyst with its ciphertext and key) |
Ciphertext-only attack
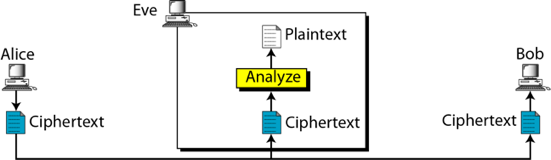
Known-plaintext attack

Chosen-plaintext attack
Chosen-ciphertext attack